Scope of the Document
The Virtual Machine model defines the view of the machine to user mode programs. User mode programs are executed in the unprivileged mode. Consequently, the privileged mode instructions cannot be used by them. Their memory view and registers available are also limited. This restricted model is discussed below.
Virtual Machine Organisation
The XSM virtual machine model defines the machine model provided by XSM to a program running in user mode. This model comprises of a restricted subset of the machine registers, a restricted instruction set and a restricted memory address space (called the virtual/logical address space).
Registers
The XSM architecture maintains several registers and ports, each capable of storing a number/string, out of which, only some are accessible in unprivileged mode. The registers available in the unprivileged mode are
| Registers | Purpose |
|---|---|
| R0-R19 | General purpose program registers |
| BP, SP, IP | Base, Stack and Instruction Pointers |
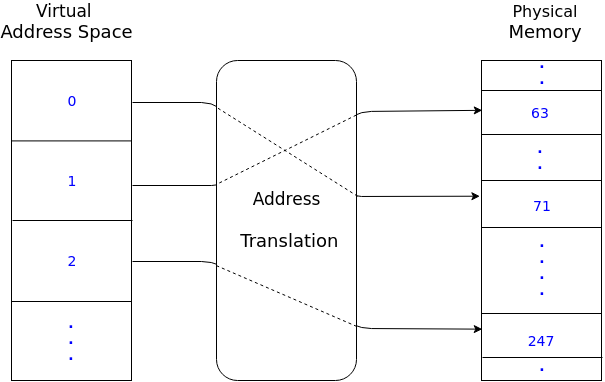
Virtual (Memory) Address Space
The virtual (or logical) memory addresses that can be generated by a user mode program is determined by the value of the PTLR register. The virtual address space of a user mode program is a contiguous address space starting from 0 to 512*PTLR-1. The virtual addreses generated by a user mode program are translated into physical addresses by the address translation scheme of XSM. The user mode program is oblivious to the address translation.
Operating systems using the XSM architecture typically specifies the maximum value of PTLR permitted for its user processes and divide the allocated address space for an application into library, code, data, stack, heap etc.
Interrupts
Software Interrupts (traps) are the mechanisms by which user mode programs can transfer control to the code that runs in the kernel mode. Software interrupt service routines typically contain the OS code for various system calls. Upon return from a software interrupt, execution resumes from the next instruction in the user mode program. A total of 15 software interrupts are available to a user mode program (Interrupt 4 - Interrupt 18).
Instruction Set
Every instruction in XSM is two words long. The unprivileged instructions are categorized into :